Crafting a threat assessment can seem tricky at first glance, but it's a skill that can be mastered with some guidance and practice. Whether you're managing risks for an organization or evaluating potential threats in a community setting, understanding how to compile a thorough threat assessment is crucial. This guide will walk you through the process step-by-step, offering practical insights and tips to make the task less daunting.
Getting Started: Define the Scope
Before diving into the details, it's vital to clarify the scope of your threat assessment. Think about the purpose of the assessment and what specific threats you need to address. Are you evaluating physical security risks for a building, cyber threats for a company, or potential hazards in an event? Narrowing down the scope will help focus your efforts and resources.
Let's say you're tasked with assessing threats for a corporate office. You might consider:
- Physical access points and vulnerabilities
- Cybersecurity measures and data protection
- Employee safety protocols
- Potential environmental risks
By defining the scope, you establish a clear framework that guides the rest of your assessment process.
Identify Key Assets and Resources
Every threat assessment revolves around protecting valuable assets. Start by identifying what you're trying to safeguard. This could include tangible assets like buildings and equipment, as well as intangible assets such as data and intellectual property.
For example, in a university setting, key assets might include:
- Student and staff data systems
- Research facilities
- Campus infrastructure
- Reputation and public image
Understanding what you need to protect ensures that your threat assessment remains focused and effective. It also helps prioritize resources and actions according to the value and vulnerability of each asset.
Evaluate Potential Threats
Once you've identified the assets, the next step is to evaluate potential threats. Consider all possible sources of harm, whether they're internal, external, natural, or human-made. A comprehensive approach will help uncover threats that might otherwise be overlooked.
To illustrate, let's look at a hospital. Potential threats could include:
- Cyberattacks targeting patient data
- Power outages affecting critical medical equipment
- Natural disasters like earthquakes or floods
- Security breaches or unauthorized access
Creating a list of potential threats allows you to systematically analyze each one, considering factors such as likelihood and potential impact.
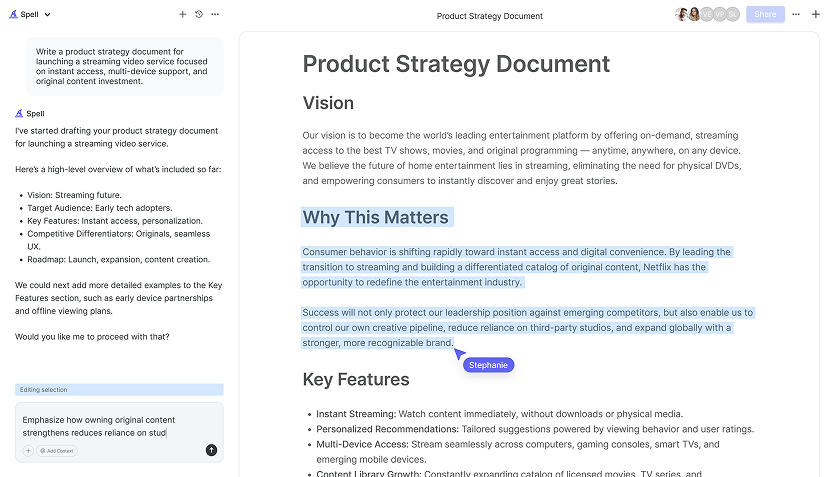
Analyze Vulnerabilities
After identifying potential threats, the next logical step is to analyze vulnerabilities. These are weaknesses that could be exploited by threats, resulting in harm to your assets. It's essential to be thorough in this analysis to create an effective threat assessment.
Consider conducting a vulnerability assessment by:
- Reviewing security protocols and procedures
- Analyzing past incidents and their causes
- Conducting interviews with key personnel
- Utilizing technology for penetration testing
For instance, in a retail store, vulnerabilities might include poor surveillance coverage, outdated alarm systems, or lack of staff training on emergency procedures. By identifying these vulnerabilities, you can develop strategies to mitigate them efficiently.
Assess the Likelihood and Impact of Threats
With a list of potential threats and vulnerabilities in hand, it's time to assess the likelihood and potential impact of each threat. This step involves evaluating how probable a threat is and the extent of harm it could cause.
Consider a simple risk matrix to evaluate threats:
- Likelihood: Rate threats as low, medium, or high probability.
- Impact: Assess the potential consequences as minor, moderate, or severe.
For example, a cyberattack on a financial institution might be rated as high likelihood and severe impact due to the sensitive nature of the data involved. This assessment helps prioritize responses and resources to address the most pressing threats first.
Develop Mitigation Strategies
Once you've assessed the threats, it's time to develop strategies to mitigate them. This involves creating plans to reduce vulnerabilities and minimize the impact of threats. Effective mitigation strategies are proactive and comprehensive.
Consider these approaches:
- Preventive measures: Implement security upgrades, such as firewalls, surveillance systems, or access controls.
- Response plans: Develop detailed response protocols for different threat scenarios.
- Training and awareness: Educate employees on recognizing and responding to threats.
- Regular reviews: Schedule periodic assessments to update and improve threat mitigation strategies.
In a school setting, this might involve installing security cameras, conducting regular drills, and implementing strict visitor policies. By taking these actions, you reduce the likelihood of threats and enhance overall security.
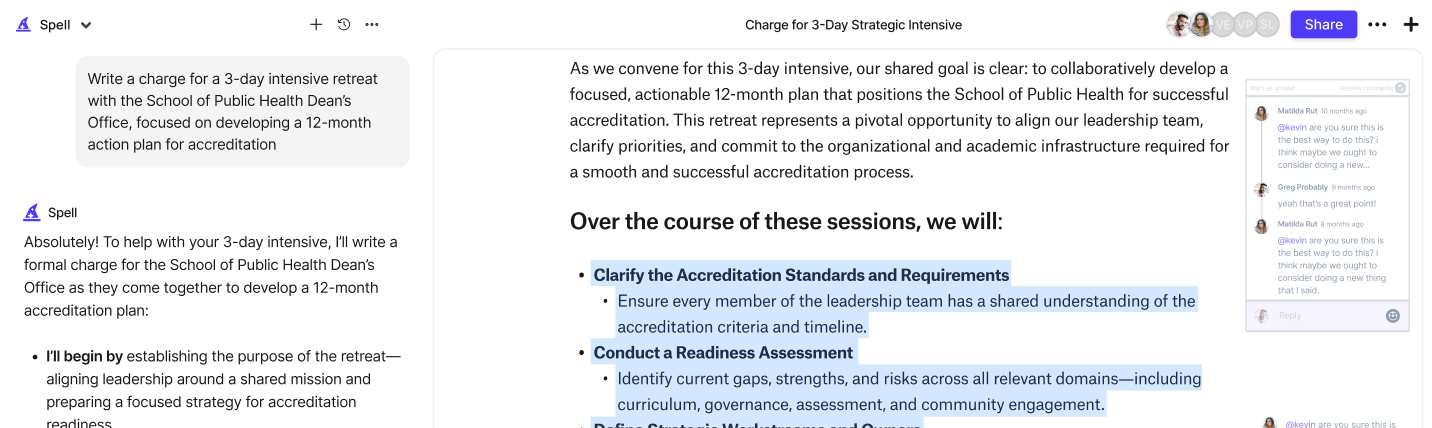
Document the Threat Assessment
Documenting your threat assessment is crucial for accountability and future reference. A well-documented assessment serves as a record of your findings and decisions, providing a basis for ongoing improvements.
Here's a basic outline of what your document might include:
Threat Assessment Report
1. [Introduction](/resources/how-to-write-an-introduction)
- Purpose
- Scope
2. Asset Identification
- List of key assets
3. Threat Evaluation
- Identified threats
4. Vulnerability Analysis
- Found vulnerabilities
5. Risk Assessment
- Likelihood and impact ratings
6. Mitigation Strategies
- Proposed actions
7. [Conclusion](/resources/how-to-write-a-conclusion)
- Summary of findings
This format ensures that all critical information is covered, making it easier for stakeholders to understand and act upon the assessment.
Communicate and Implement the Findings
Effective communication is key to implementing your threat assessment findings. Share the report with relevant stakeholders, ensuring clarity and understanding across the board.
Here's how you might go about it:
- Present the findings: Hold a meeting to discuss the assessment and highlight key points.
- Assign responsibilities: Clearly define who is responsible for implementing each mitigation strategy.
- Set timelines: Establish deadlines for implementing various actions.
- Ensure follow-up: Schedule regular check-ins to monitor progress and address any issues.
Remember, the goal is to foster a collaborative environment where everyone understands their role in maintaining security. By communicating effectively, you set the stage for successful implementation.
Review and Update the Threat Assessment
A threat assessment is not a one-time task. It requires regular review and updates to remain effective. As new threats emerge and circumstances change, your assessment should evolve to reflect these developments.
Consider these steps for continuous improvement:
- Schedule regular reviews: Set a timeline for periodic assessments, such as annually or bi-annually.
- Monitor changes: Keep an eye on evolving threats, technologies, and organizational changes.
- Incorporate feedback: Use input from stakeholders to refine and enhance your assessment.
- Update documentation: Revise your threat assessment document to reflect any changes.
By making regular updates, you ensure that your threat assessment remains relevant and effective, providing ongoing protection for your organization or community.
Using Technology to Enhance Threat Assessments
Incorporating technology into your threat assessment process can offer valuable insights and efficiencies. Tools like Spell can simplify documentation and collaboration, allowing you to focus on analysis and strategy development.
Here's how Spell can help:
- Document creation: Generate and refine threat assessment reports quickly using AI-powered tools.
- Collaboration: Work with your team in real-time, sharing insights and updates seamlessly.
- Editing: Use natural language prompts to edit and improve your documents without leaving the platform.
By leveraging technology, you can streamline your threat assessment process and produce high-quality, actionable reports more efficiently.
Final Thoughts
Writing a threat assessment can be an intricate task, but with a structured approach, it becomes manageable. From defining the scope to developing mitigation strategies, each step builds toward a comprehensive evaluation of potential risks. Remember, tools like Spell can assist in crafting clear, professional documents, helping you focus on what matters most. Keeping people and assets safe.






