So, you've got the task of writing a security incident report, and you're staring at a blank screen wondering where to start. Don't worry, you're in good company. Writing these reports can be tricky, but they're crucial for maintaining safety and accountability in any organization. Let's break down the process into manageable steps, so you can create a report that's clear, detailed, and useful.
Why Security Incident Reports Matter
Before diving into the 'how,' let‘s chat about the 'why.' Security incident reports are the unsung heroes of organizational safety. They provide a detailed account of events that compromise security, helping to prevent future incidents. Think of them as a tool for learning and improvement. They not only document what went wrong, but also guide teams on how to fix vulnerabilities.
For instance, if a security breach occurs, a well-documented report helps pinpoint what went awry and why. Without these reports, organizations could repeatedly face the same issues, like a hamster in a wheel. Lots of running, but no progress.
Setting the Scene: Start With the Basics
Your report should start with the basic details: the who, what, when, and where of the incident. This section sets the foundation for everything else.
- Who: Identify everyone involved in the incident, from those who witnessed it to those affected by it.
- What: Describe what happened. Was it a data breach, a physical security incident, or something else?
- When: Note the date and time of the incident. Accurate timing can be crucial for understanding the sequence of events.
- Where: Specify the location. Was it in a specific office, a server room, or a public area?
Here's an example of how this might look:
Incident Report
Date: October 15, 2023
Time: 3:45 PM
Location: Server Room B
Reported By: Jane Doe
Involved Parties: John Smith (IT Analyst), ABC Security Team
Description: Unauthorized access detected in Server Room B.
Telling the Story: Describe the Event in Detail
Once you've laid out the basics, it's time to dive into the details. Think of this section like telling a story. You're painting a picture of what happened, step by step.
Start by describing the sequence of events. How did the incident unfold? What were the immediate actions taken? Use clear, concise language and avoid jargon that might confuse readers unfamiliar with technical terms.
For example:
At 3:45 PM, John Smith noticed suspicious activity on the security monitoring system. He immediately informed the ABC Security Team. Upon arrival, the team discovered that an unauthorized person was attempting to access the servers. The intruder was apprehended and escorted from the premises.
Analyzing the Incident: Identify Causes and Effects
Once you've laid out the sequence of events, it's time to dig deeper. What caused the incident? What were the consequences? This section is all about connecting the dots and understanding the root of the problem.
Consider questions like:
- Was there a failure in security protocols?
- Were there any warning signs that were ignored?
- What systems or data were affected by the incident?
Example analysis:
Analysis: The incident was caused by a failure in the security system, which did not alert the team in real-time. This allowed the intruder to gain access to sensitive areas. As a result, confidential data was exposed, potentially compromising client privacy.
Response and Resolution: What Was Done?
Now, let's move on to how the incident was handled. Document the immediate actions taken to resolve the issue, as well as any follow-up measures. This section shows how the organization responded and what steps were taken to mitigate damage.
For instance:
Response: The ABC Security Team secured the area and escorted the intruder off the premises. The IT department immediately conducted a system audit to assess any data breaches. All affected systems were temporarily shut down and rebooted with updated security protocols.
Recommendations: Preventing Future Incidents
Every incident is a learning opportunity. Use this section to recommend actions that could prevent similar incidents in the future. These could include changes to security protocols, staff training, or updates to technology.
Example recommendations:
Recommendations:
1. Implement real-time alert systems to notify security personnel of unauthorized access attempts.
2. Conduct regular security training for all staff to recognize and respond to potential threats.
3. Upgrade the existing security software to include more comprehensive monitoring capabilities.
Documenting the Findings: The Importance of Accuracy
Accuracy is critical when writing a security incident report. The document may be used in legal proceedings or as part of an internal review, so it needs to be precise and free from bias.
Check your facts, verify witness statements, and ensure all details are supported by evidence. If you're unsure about something, it's better to state that clearly than to guess.
Getting Feedback: Collaborate With Colleagues
Before finalizing your report, it‘s a good idea to get feedback from colleagues. They might catch details you missed or provide additional insights that enhance the report.
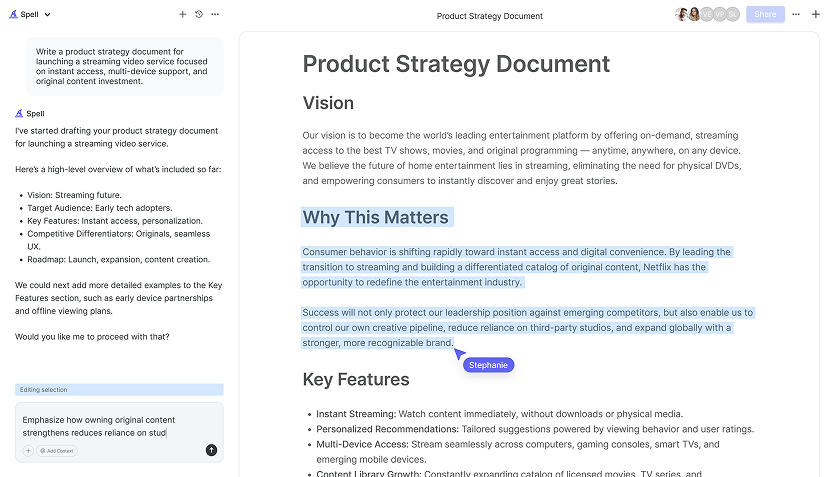
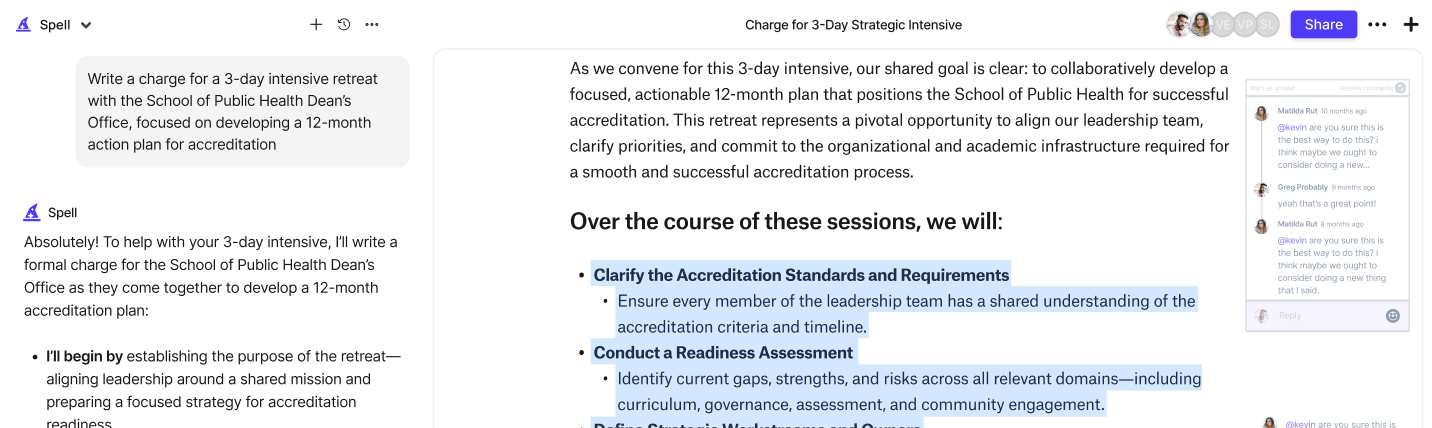
Consider using a tool like Spell for real-time collaboration. It's like Google Docs with AI built in, making it easier to draft, edit, and refine your report with input from your team.
Finalizing the Report: Review and Revise
With feedback in hand, it's time to polish your report. Check for clarity, coherence, and conciseness. Make sure the report flows logically and that all sections are complete.
Here's where Spell can help again. You can quickly make revisions and ensure your document is clear and professional. It's like having an AI editor that helps you maintain quality and consistency throughout your report.
Final Thoughts
Writing a security incident report may seem daunting at first, but by breaking it down into these steps, you can create a comprehensive and useful document. Remember to focus on the facts, provide detailed descriptions, and suggest improvements. And when you need an extra hand, Spell is there to help streamline the process, making collaboration and editing a breeze.






