Crafting a security policy might sound like a dry task, but it's one of those things that you'll be grateful for when you need it most. Think of it as a safety net for your organization. In this post, we'll unpack what makes an effective security policy, step by step, with plenty of examples and tips along the way. Whether you're starting from scratch or looking to improve an existing policy, you're in the right place.
Why a Security Policy Matters
You might wonder, why go through the hassle of writing a security policy at all? Well, think of it like this. A security policy acts as a shield for your company's most valuable assets. It's the set of rules that helps protect your informational crown jewels from theft, misuse, or damage. A well-crafted policy ensures everyone knows what's expected, minimizing risks and keeping things running smoothly.
Imagine a company where every employee knows precisely what to do if they suspect a data breach. That's the power of a solid security policy. It's not just about mitigating risks. It's about creating a culture of security awareness and responsibility. This becomes particularly vital in our digital world where cyber threats are lurking around every corner.
Identifying Your Security Needs
Before you start writing, it's crucial to pinpoint what your organization needs from a security policy. This step involves assessing the current security landscape and identifying potential vulnerabilities. Here's a simple way to kick things off:
- Conduct a Risk Assessment: Look at the possible threats your organization faces. Be it data breaches, insider threats, or even natural disasters.
- Understand Your Assets: Know what you're protecting. This could be anything from customer data to proprietary technology.
- Evaluate Current Security Measures: What's already in place? Identify gaps and areas for improvement.
Take a moment to imagine you're the CEO of a mid-sized tech company. Your assets include sensitive customer data and software codes. A risk assessment might reveal potential vulnerabilities in your data storage systems. With this knowledge, you can tailor your policy to address these specific risks.
Setting Clear Objectives
Once you've identified your security needs, the next step is setting clear objectives for your policy. These objectives act as the guiding principles for your security measures. Here's how you can define them:
- Align with Business Goals: Ensure your security objectives support your company's overall mission and strategy.
- Prioritize Risks: Not all risks are created equal. Focus on mitigating the ones that pose the greatest threat to your business.
- Define Success Metrics: How will you measure the effectiveness of your security policy? Consider setting benchmarks for compliance or incident response times.
For instance, if your company's goal is to expand internationally, your security objectives might include protecting intellectual property and ensuring compliance with international regulations. By aligning your policy with these goals, you create a security framework that supports your business's growth.
Structuring Your Security Policy
Now that you've set your objectives, it's time to structure your policy. A well-organized policy is easier to follow and enforce. Consider these key components:
- Introduction: Outline the purpose of the policy and its importance to the organization.
- Scope: Define who the policy applies to and what assets it covers.
- Policy Statements: Clearly state the rules and expectations for behavior.
- Roles and Responsibilities: Specify who is responsible for implementing and maintaining the policy.
- Compliance: Outline the consequences for non-compliance and the process for handling violations.
Here's a quick example of a policy statement:
All employees must use complex passwords that include a mix of letters, numbers, and symbols. Passwords must be changed every 90 days.
This statement is clear and actionable, leaving no room for ambiguity.
Writing Clear and Concise Policy Statements
When writing policy statements, clarity is your best friend. You want your policy to be easy to understand and follow. Here are some tips to get it right:
- Use Plain Language: Avoid jargon and technical terms that might confuse readers.
- Be Specific: Vague statements are hard to enforce. Be precise about what is required.
- Focus on Action: Use active voice and direct language to communicate expectations.
Consider this example of a well-written policy statement:
Employees must lock their computer screens when leaving their desks to prevent unauthorized access.
It's simple, direct, and leaves no room for misinterpretation.
Incorporating Legal and Regulatory Requirements
Your security policy must comply with legal and regulatory requirements relevant to your industry. Failure to do so can result in hefty fines or legal action. Here's how to ensure compliance:
- Research Regulations: Understand the laws and regulations that apply to your business, such as GDPR or HIPAA.
- Seek Legal Advice: Consult with legal experts to ensure your policy meets all necessary criteria.
- Update Regularly: Laws change, and so should your policy. Regularly review and update your policy to maintain compliance.
For instance, if your organization handles personal data of EU citizens, your policy must address GDPR requirements, such as data protection and privacy rights.
Engaging Stakeholders in the Process
A security policy is only effective if everyone in the organization supports and follows it. Engaging stakeholders in the creation process can increase buy-in and compliance. Here's how to get them on board:
- Involve Key Departments: Get input from IT, HR, and legal teams to ensure all angles are covered.
- Communicate Benefits: Clearly explain how the policy protects employees and the organization.
- Provide Training: Offer training sessions to educate employees on the policy and its importance.
Imagine you're introducing a new access control policy. By involving the IT team in its development, you ensure technical feasibility and gain their support for implementation.
Implementing and Enforcing the Policy
Writing the policy is just the beginning. Implementation and enforcement are where the rubber meets the road. Here's how to make it happen:
- Communicate Clearly: Ensure all employees are aware of the policy and understand their responsibilities.
- Monitor Compliance: Regularly check for adherence to the policy and address non-compliance promptly.
- Review and Revise: Periodically review the policy's effectiveness and make necessary adjustments.
Think of it like maintaining a car. Regular checks and maintenance keep it running smoothly. Similarly, regular policy reviews ensure your security measures remain effective and relevant.
The Role of Technology in Security Policies
Technology plays a vital role in implementing and enforcing security policies. From access controls to monitoring tools, the right tech can significantly enhance your organization's security posture. Here's how:
- Access Control Systems: Use technology to restrict access to sensitive areas and data.
- Monitoring Tools: Implement tools to track compliance and detect potential breaches.
- Automated Alerts: Set up alerts to notify relevant parties of suspicious activities.
For example, implementing a multi-factor authentication system can add an extra layer of security, making it harder for unauthorized users to gain access.
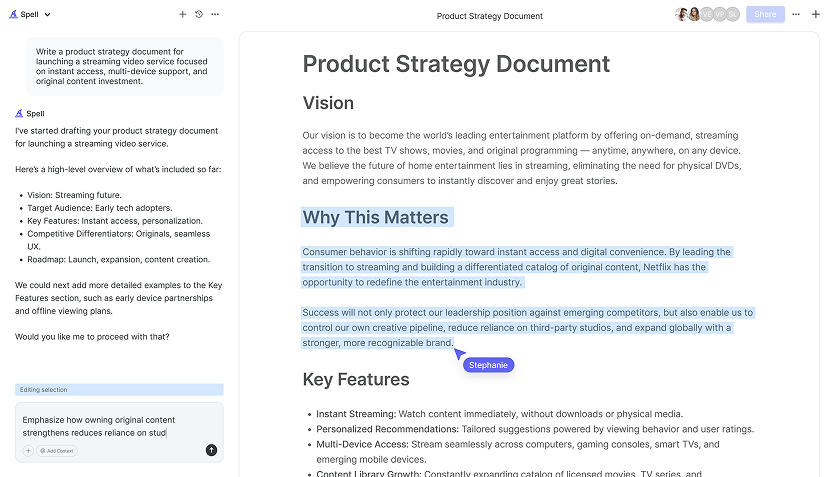
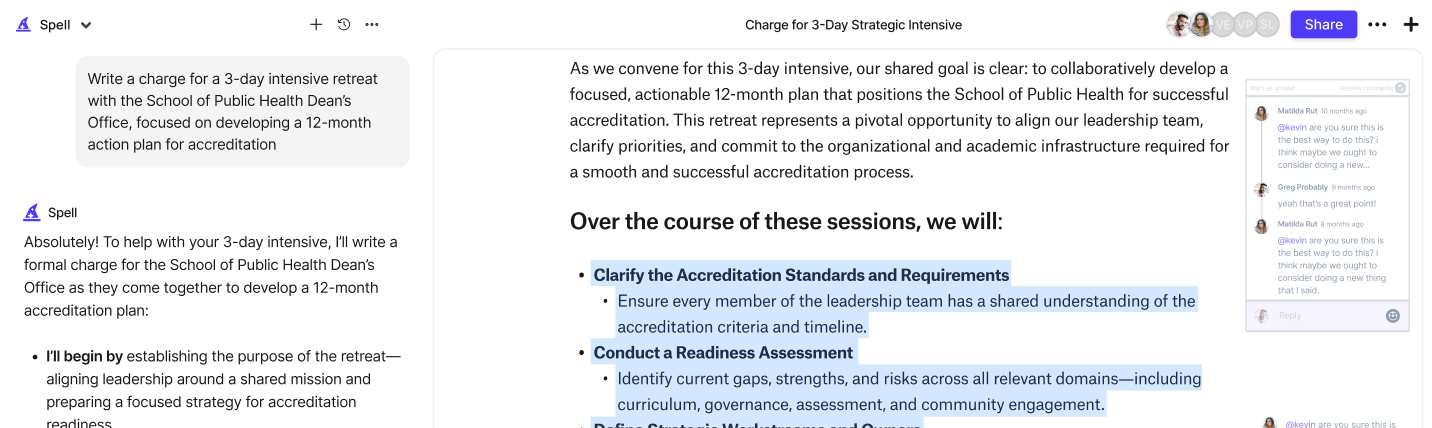
Using Spell to Streamline Policy Creation
Creating a security policy can be time-consuming, but it doesn't have to be. With Spell, you can draft, refine, and perfect your policy in a fraction of the time. Spell's AI-driven editor helps you generate high-quality content quickly and efficiently, leaving you with more time to focus on implementation and enforcement.
Final Thoughts
Writing a security policy might not be the most glamorous task, but it's a crucial one. With a clear understanding of your organization's needs and a structured approach, you can craft a policy that protects your assets and supports your business goals. And remember, with the help of Spell, you can make the process faster and more efficient, allowing you to focus on what truly matters. Keeping your organization safe and secure.






